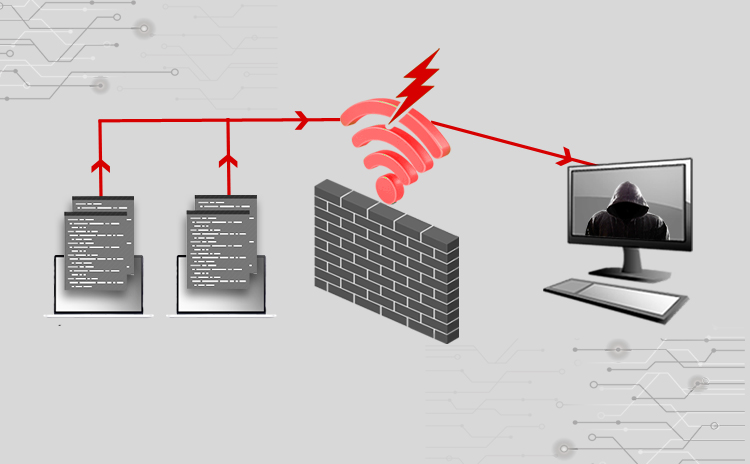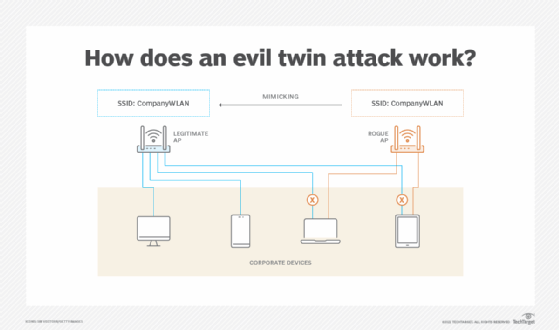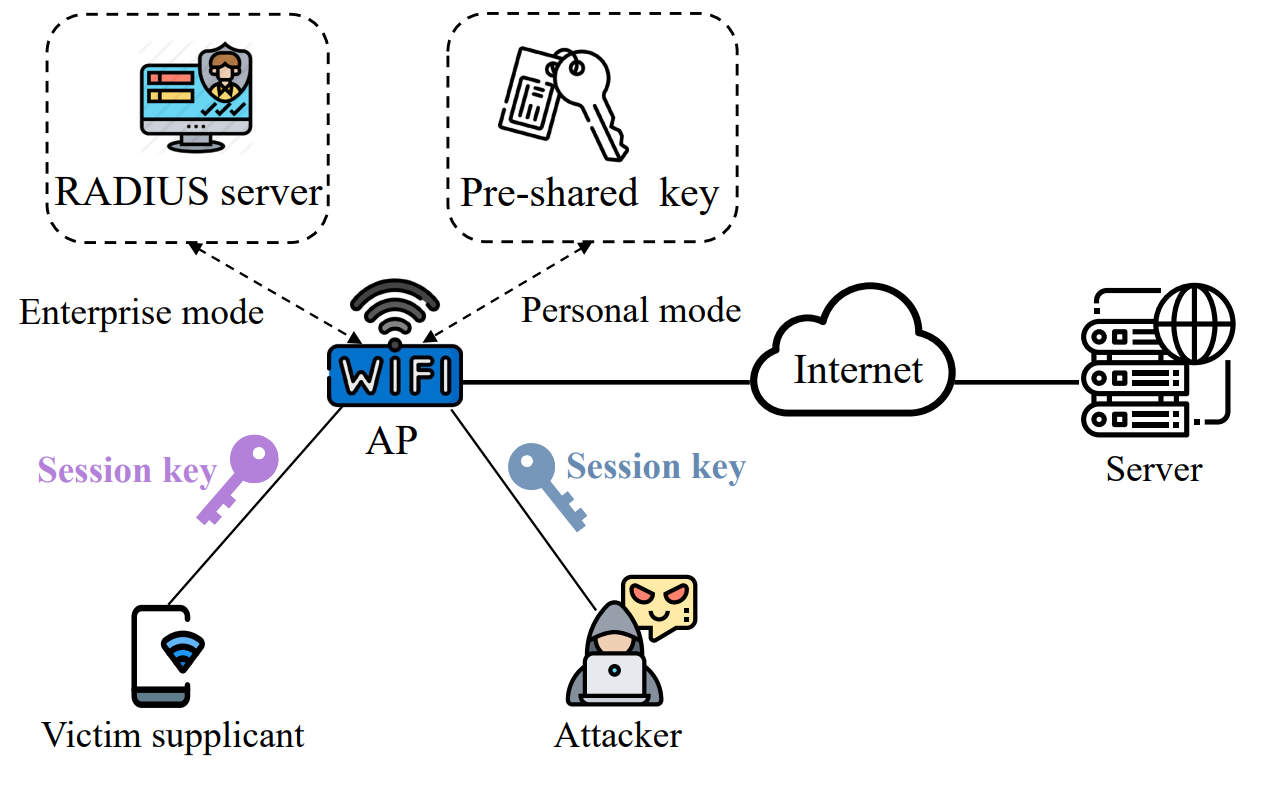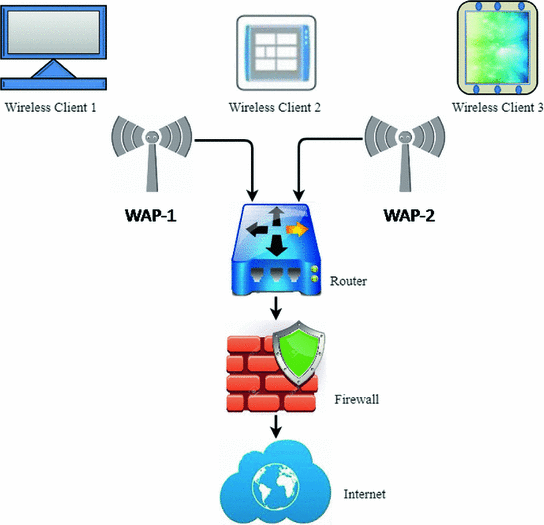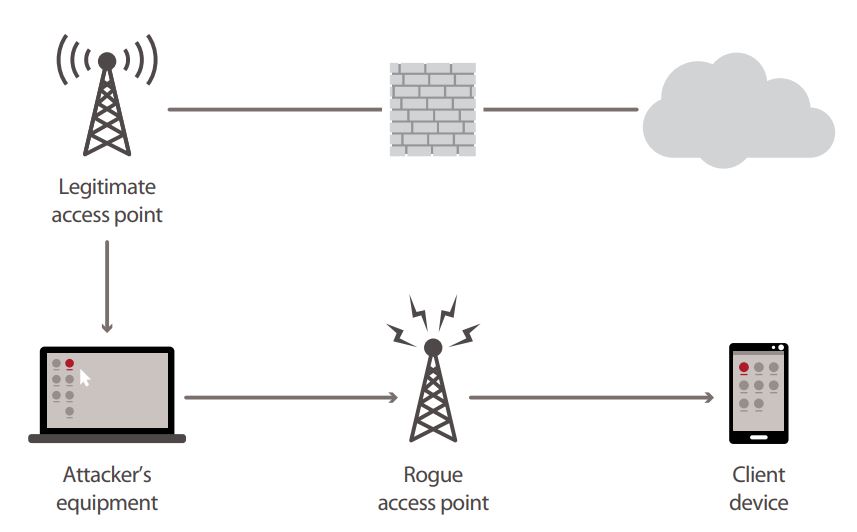
Network Security : WiFi Security fixation | Pune Mumbai Hyderabad Delhi Bangalore India | Valency Networks
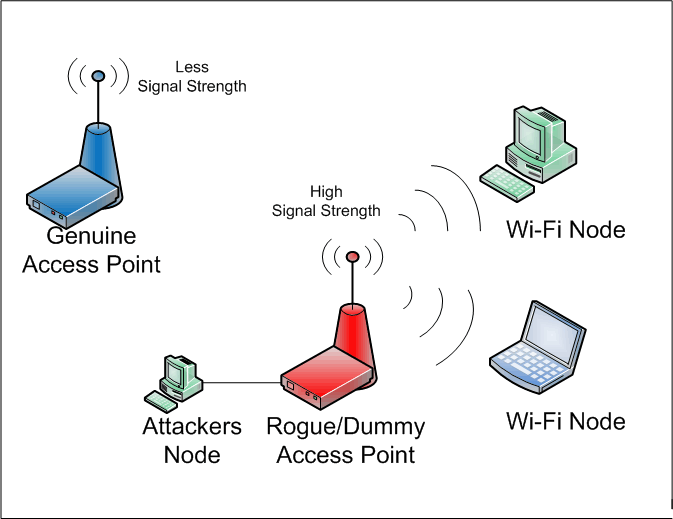
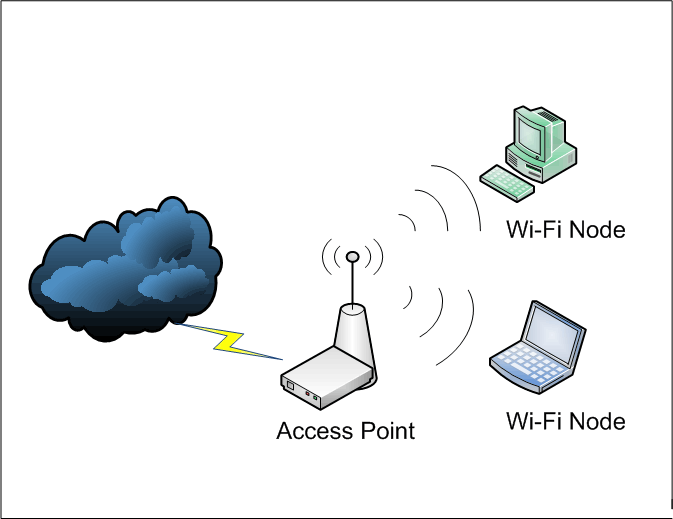
Network Security : WiFi Security fixation | Pune Mumbai Hyderabad Delhi Bangalore India | Valency Networks
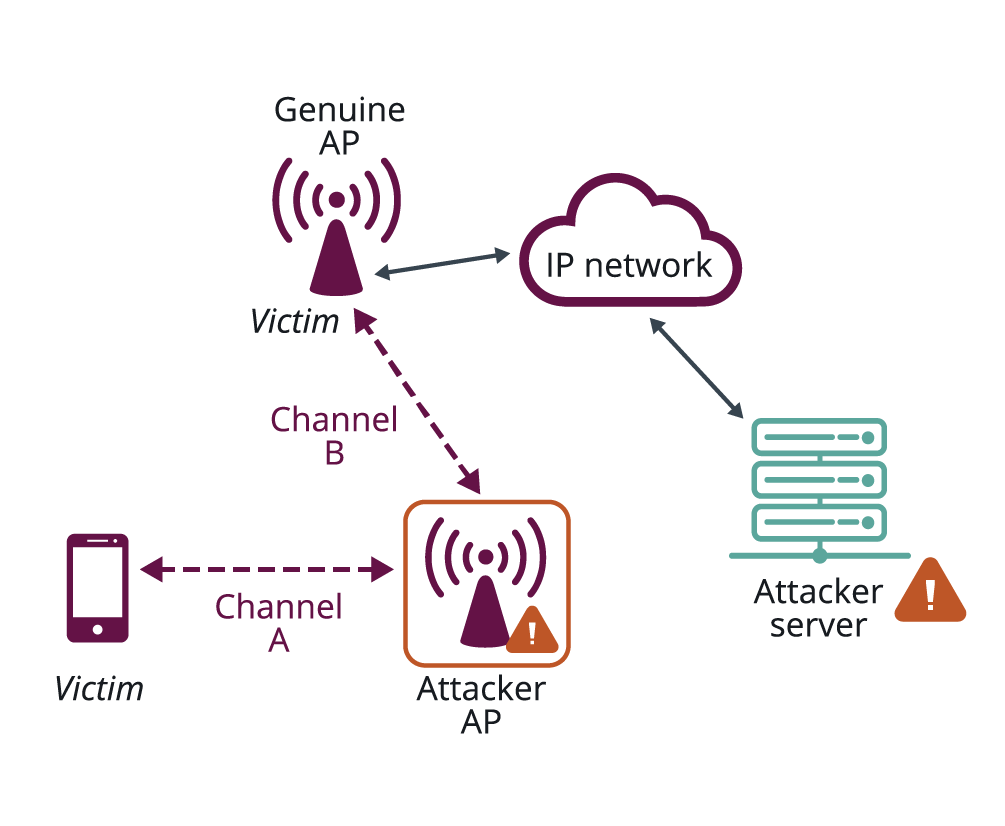
Wi-Fi CERTIFIED WPA3™ December 2020 update brings new protections against active attacks: Operating Channel Validation and Beacon Protection | Wi-Fi Alliance